Wednesday, July 28, 2010
Top Ways to Increase the Battery Life of Your Laptop
Jan
Few days back i purchased my Dell Studio 1558 laptop and everything is working fine with my system. Now the thing which comes in most of the laptop user's mind is, about the Battery life and performance of their system. So the same thing comes in my mind too. So i Google and found these simple, short and easy steps to increase the battery life of your Laptop.
Following ways will increase the productivity and efficiency of your system.
1. Defrag regularly - The faster your hard drive rotates, the faster it can handle input/output operations. Thus managing your disk space by defragmenting your hard drive will increase your laptop's battery life. Make your hard drive as efficient as possible by defragging it regularly. (but not while it’s on battery of course!)
2. Close running programs in the background - Shut down everything that isn’t crucial when you’re on battery.
3. Cut down external devices(USB/TV Cards) – USB devices (including your mouse) & WiFi drain down your laptop battery. Remove or shut them down when not in use. USB devices if plugged in they suck up energy even when not in use (those shiny lights take electricity which gets sucked from your laptops battery).
4. Increase RAM - This will allow you to process more with the memory your laptop has, rather than relying on virtual memory.
5. Keep the battery contacts clean
6. Take care of your battery – Do not leave a charged battery for long periods of time. Once charged, you should at least use the battery at least once every two to three weeks. Also, do not let a Li-On battery completely discharge.
7. Hibernate rather than Standby – Hibernating a PC will actually save your PC’s state as it is, and completely shut itself down.
8. Keep operating temperature down - Your laptop operates more efficiently when it’s cooler. Clean out your air vents with a cloth or keyboard cleaner.
9. Set up and optimize your power options – Go to ‘Power Options’ in your windows control panel and set it up so that power usage is optimized (Select the ‘max battery’ for maximum effect).
10. Don’t multitask – Do one thing at a time when you’re on battery. Rather than working on a spreadsheet, letting your email client run in the background and listening to your latest set of MP3′s, set your mind to one thing only. If you don’t you’ll only drain out your batteries before anything gets completed!
11. Go easy on the PC demands – The more you demand from your PC. Passive activities like email and word processing consume much less power than gaming or playing a DVD. If you’ve got a single battery charge – pick your priorities wisely.
12. Get yourself a more efficient laptop
13. Prevent the Memory Effect - If you’re using a very old laptop, you’ll want to prevent the ‘memory effect’ – Keep the battery healthy by fully charging and then fully discharging it at least once every two to three weeks. Exceptions to the rule are Li-Ion batteries (which most laptops have) which do not suffer from the memory effect.
14. Dim your screen – Most laptops come with the ability to dim your laptop screen. Some even come with ways to modify CPU and cooling performance. Cut them down to the lowest level you can tolerate to squeeze out some extra battery juice.
Friday, July 23, 2010
Dos and Don’ts to protect your computer from Viruses and Malicious Internet Programs
Jan
So after reading a lot from internet and making a good collection of tips about what to do and not to do on internet.
Here is the list of dos and don'ts for protecting your computer from unwanted internet worms, Viruses and Malicious Internet Programs :
PayPal in Pakistan??
Jan
PayPal in Pakistan Looks Possible, but it May Take Time!
Talk of PayPal entering Pakistan got buzzed up in previous 2 days, especially after some professionals got involved in discussion on TGP.
As always, Fouad Bajwa was amongst the campaigners, who announced that Mr. Ibrahim Qureshi (Director Raffles Pvt. Ltd) has promised to voice the need of PayPal in Pakistan during Obama’s presidential summit.
Discussion caught further attention when a member revealed that Paypal’s advance team recently visited Pakistan. He further said that PayPal is already engaged withlocal lawyers and other related institutes to start building their infrastructure to offer Paypal services in Pakistan.
This looked quite fascinating and importantly it made sense, particularly, after a recent announcement by PayPal to aggressively campaign in Asia (to be number one in region like they are in Europe and America) with an evident focus towards the mobile commerce along with traditional e-commerce services.
For the purpose, PayPal announced last month to double its employees from 1000 to over 2000 this year, with 100 new jobs alone for Singapore, company’s regional headquarter.
Though, PayPal has officially not authorized all this. Anuj Nayar, Director, Global Communications at PayPal in a communication with ProPakistani accepted that like always, PayPal is looking at ways to grow the business in Asia. However, he said that he has nothing in hands to announce about PayPal’s specific plans for Pakistan market.
A source at PayPal, who wanted to remain unnamed, told ProPakistani that Pakistan has some serious issues relating to its ecommerceinfrastructure , payment gateways, which make it impossible for PayPal to step in to Pakistan. He said, PayPal’s usual feature of linking an email with customers’ bank account will never be possible in given banking infrastructure of Pakistan.
He admitted that PayPal has studied Pakistan, and recognizes the potential, however, stated problem is not in hands of PayPal.
In his opinion, PayPal may start operations while accepting limited banks, probably starting with Citibank (which has payment gateway), and then rolling out solution for other banks of the country.
Regulatory issues with State Bank of Pakistan are considered as hurdles too, but as stated earlier, there is no question of arguing over regulations when there is noinfrastructure in place.
This is where our local banks and of course the government has to play some role. Payment gateways are a must have thing. We had reports of PTA working on it, but nothing concrete could be said on it, as of now.
So as a crux, one can safely say that its not PayPal who is not coming in Pakistan, its our banks who are not well equipped.
On a side note, as PayPal has plans to offer mobile banking solutions in the region, companies like EasyPaisa can come in, and join hands with PayPal (given that their banking partner– Tameer Bank, starts offering electronic payment solution).
But only time will tell that EasyPaisa and PayPal will work in hands or will become rivals.
Friday, June 18, 2010
10 Security Tips to Protect Yourself
Jan
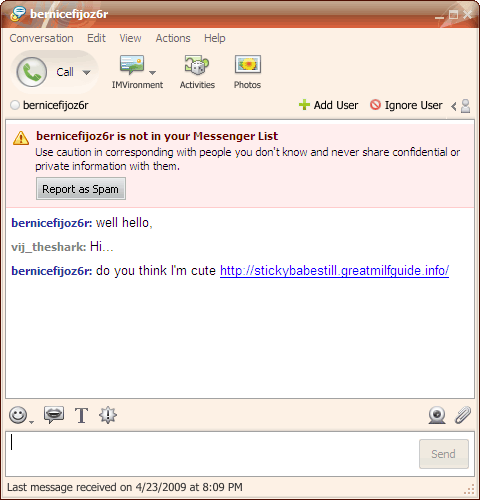
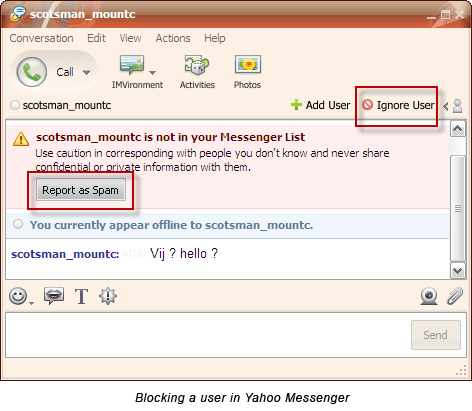
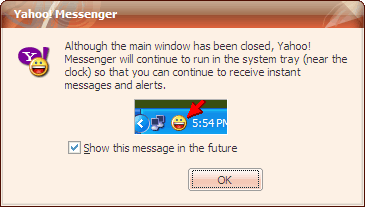
Instant Messenger Hacks: 10 Security Tips to Protect Yourself Especially in a business environment, unsecured IM installations are creating backdoors for hack attacks. This threat has increased manifold because nearly all IM’s allow for exchange of files, images, songs and even peer to peer sharing of entire folders. Also, by putting these 10 habits in place. Every IM client asks you to create a screen name. A screen name usually refers to your email ID. Create a screen name which does not touch upon personal information or your real identity. For instance, my screen name is ‘Braniac’ and not ‘Saikat’. And NEVER provide any personal details including credit cardnumbers and social security number over the internet. Always vet your contact list with people whom you know something about. Talking with Mr. Anonymous at the other end of space may be fraught with risk. It is possible to discover your computer address (i.e. your IP) from an instant message and that usually is the first requirement for a remote hack attack. Don’t believe everything you read and always verify any information or request for information. This is what a spam link might look like – This is probably what you will be bombarded with first. A link tempts you to click it just for the lark. A lot of these links take you to websites which can install spyware stealthily on your computer. For e.g. Viruses and worms with colorful names such as W32.Yalove or W32/Spybot-MQ are potential threats to Yahoo users. An IM client like Yahoo allows P2P file sharing. Do not share unknown content even if the person is known. P2P files, like email attachments can carry viruses, Trojan horses, and worms. They are engineered to seed themselves to other members on your buddy list. Be especially cautious when someone sends you an .exe or a .zip file. Yahoo has an Ignore user or Report as spam so that he can’t disturb you once again. GTalk has a Block user option. Using this option allows you to keep out the unwanted from repeatedly messaging you. The default security settings in chat software tend to be relatively lax. Thus making you open to attacks. Check the settings and preferences of your chat client to apply stricter permission controls. Most IM clients lack encryption features. That essentially means that your messages can be tracked and read by eavesdropping hackers using technologies like packet sniffers or similar ones. Passwords are also a security loophole with hardly any client using strong password encryption. The subject of encryption and strong password protection would require another post by itself. So I hand you over to Tim’s excellent post on How To Secure & Encrypt Your Instant Messaging Chats. Here at MakeUseOf.com we have a lot of posts tagged as ‘passwords’. Why not take a look at ways to set strong passwords. IM client companies spend a lot of effort behind doors to prevent backdoor threats. Newer versions come with bug fixes and enhanced security. For instance, the latest version of Yahoo IM is better integrated with anti-virus solutions like Norton Internet Security and Norton Anti-Virus. So, always update your IM client as soon as one becomes available. If the chat client does not automatically prompt for an upgrade, go to the website and check your version number with the latest available. You can note the version of your particular client by clicking on Help – About… A lot of third party plug-ins are available for download which enhance the chatting experience. It is safer and advisable to always download from the IM client websites themselves or from verified sources. It is an oft repeated habit to click on the [X] button and exit. But this action does not close our IM client completely. Most often, they continue to run in the system tray leaving it ‘open’ for a third person to access it. IMs also have a nasty habit of broadcasting your online presence even if left to run as a background task. Especially in public computers be mindful of logging out and exiting completely. Also, never click on any Remember My Password checkbox during log-in as an added safeguard. For Yahoo Users: Before you get up, delete your Yahoo Messenger profile. It is located by default at C:\Program Files\Yahoo!\Messenger\Profiles. Sometimes we will click a link; sometimes we will download a file. All the precautions in the world will not be able to protect us if we don’t have a secure browser, a good firewall and an anti-virus updated with the latest virus signatures. These three not only protect us from IM attacks but they are the must-haves for any system. Chatting as against emailing is a real time activity. It is in that sense more social than any other form of web communication. The danger is that chatting can lull us into a false sense of security. Just a few fundamental forethoughts help us to turn that false sense into a more conscious sense of security.
Ignore them.
How to Secure your E mail Address while posting them on websites.
Jan
How to stop spams
Sometimes we have to post the email id on some sites, this will increase the chances of getting spams in your inbox.
So follow some techniques and you ll know the safer way to post e mail address on websites
Replace the AT (@) and DOT (.) symbols:
a.p.agarwaal AT gmail DOT com
a.p.agarwaal (at) gmail.com
a.p.agarwaal@gmail.com
a.p.agarwaal_AT_gmail_DOT_com
Replace text with an image:
This technique involves creating a graphic or screen capture of your email address text in jpg, png or gif formats and display that picture instead of the actual address string. Robots and spiders can't read the text that is embedded in the image. Anyone who wants to email you will have to manually type in your address though.
Email Obfuscators
E-mail Obfuscator make you email less vulnerable to spammers. Using an online email Obfuscator, convert (or disguise) individual characters of your email address into corresponding ASCII code (a <=> a hex coding) For example, the email address a@b.com is represented in ASCII as:
a@b.com
The above ASCII string can be used as arguement for mailto: HTML tag as shown here. Email addresses will appear perfectly normal, and will even be clickable, to human visitors to your website.