Friday, June 18, 2010
10 Security Tips to Protect Yourself
Jan
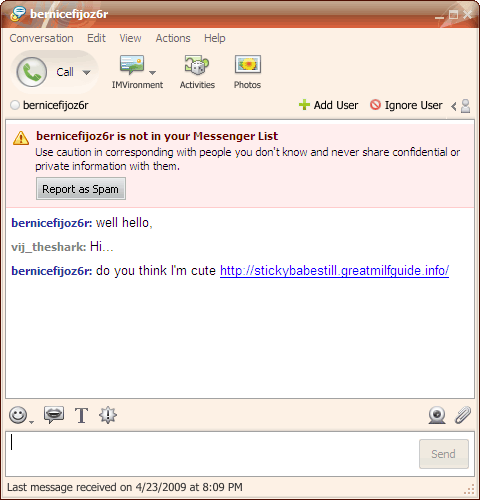
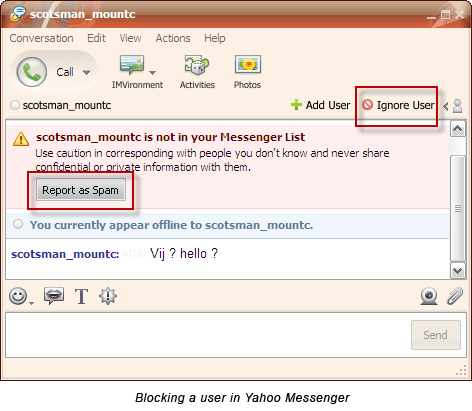
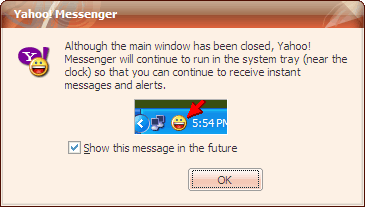
Instant Messenger Hacks: 10 Security Tips to Protect Yourself Especially in a business environment, unsecured IM installations are creating backdoors for hack attacks. This threat has increased manifold because nearly all IM’s allow for exchange of files, images, songs and even peer to peer sharing of entire folders. Also, by putting these 10 habits in place. Every IM client asks you to create a screen name. A screen name usually refers to your email ID. Create a screen name which does not touch upon personal information or your real identity. For instance, my screen name is ‘Braniac’ and not ‘Saikat’. And NEVER provide any personal details including credit cardnumbers and social security number over the internet. Always vet your contact list with people whom you know something about. Talking with Mr. Anonymous at the other end of space may be fraught with risk. It is possible to discover your computer address (i.e. your IP) from an instant message and that usually is the first requirement for a remote hack attack. Don’t believe everything you read and always verify any information or request for information. This is what a spam link might look like – This is probably what you will be bombarded with first. A link tempts you to click it just for the lark. A lot of these links take you to websites which can install spyware stealthily on your computer. For e.g. Viruses and worms with colorful names such as W32.Yalove or W32/Spybot-MQ are potential threats to Yahoo users. An IM client like Yahoo allows P2P file sharing. Do not share unknown content even if the person is known. P2P files, like email attachments can carry viruses, Trojan horses, and worms. They are engineered to seed themselves to other members on your buddy list. Be especially cautious when someone sends you an .exe or a .zip file. Yahoo has an Ignore user or Report as spam so that he can’t disturb you once again. GTalk has a Block user option. Using this option allows you to keep out the unwanted from repeatedly messaging you. The default security settings in chat software tend to be relatively lax. Thus making you open to attacks. Check the settings and preferences of your chat client to apply stricter permission controls. Most IM clients lack encryption features. That essentially means that your messages can be tracked and read by eavesdropping hackers using technologies like packet sniffers or similar ones. Passwords are also a security loophole with hardly any client using strong password encryption. The subject of encryption and strong password protection would require another post by itself. So I hand you over to Tim’s excellent post on How To Secure & Encrypt Your Instant Messaging Chats. Here at MakeUseOf.com we have a lot of posts tagged as ‘passwords’. Why not take a look at ways to set strong passwords. IM client companies spend a lot of effort behind doors to prevent backdoor threats. Newer versions come with bug fixes and enhanced security. For instance, the latest version of Yahoo IM is better integrated with anti-virus solutions like Norton Internet Security and Norton Anti-Virus. So, always update your IM client as soon as one becomes available. If the chat client does not automatically prompt for an upgrade, go to the website and check your version number with the latest available. You can note the version of your particular client by clicking on Help – About… A lot of third party plug-ins are available for download which enhance the chatting experience. It is safer and advisable to always download from the IM client websites themselves or from verified sources. It is an oft repeated habit to click on the [X] button and exit. But this action does not close our IM client completely. Most often, they continue to run in the system tray leaving it ‘open’ for a third person to access it. IMs also have a nasty habit of broadcasting your online presence even if left to run as a background task. Especially in public computers be mindful of logging out and exiting completely. Also, never click on any Remember My Password checkbox during log-in as an added safeguard. For Yahoo Users: Before you get up, delete your Yahoo Messenger profile. It is located by default at C:\Program Files\Yahoo!\Messenger\Profiles. Sometimes we will click a link; sometimes we will download a file. All the precautions in the world will not be able to protect us if we don’t have a secure browser, a good firewall and an anti-virus updated with the latest virus signatures. These three not only protect us from IM attacks but they are the must-haves for any system. Chatting as against emailing is a real time activity. It is in that sense more social than any other form of web communication. The danger is that chatting can lull us into a false sense of security. Just a few fundamental forethoughts help us to turn that false sense into a more conscious sense of security.
Ignore them.
Saturday, June 12, 2010
Delete Wordpress Spam comments
Jan
In Wordpress, table wp_comments holds the details related all the comments on your blog. It has specific columns related to the information for the comments. One of the most important column is the comment_approved which holds the status of each comment. The column can take one of the three possible values for any comment. The possible values are 1, 0 and spam.
You can also get the possible values by running the below mentioned query against the database.
Below is the legend for the various values that can be present in the comment_approved column of the wp_comments table.select distinct(comment_approved) from wp_comments; +------------------+ | comment_approved | +------------------+ | 0 | | 1 | | spam | +------------------+ 3 rows in set (0.00 sec)
0 = Comment Awaiting Moderation.
1 = Approved Comment
spam = Comment marked as Spam.
Now, lets type in a query which fetches us all the comments and groups them in specific categories.
The query above tells us that we have 452 comments marked as Spam. Now, in order to delete these comments, we need another query, which targets the spam comments and deletes them from the wp_comments table.select count(comment_approved), comment_approved from wp_comments group by comment_approved ; +-------------------------+------------------+ | count(comment_approved) | comment_approved | +-------------------------+------------------+ | 1 | 0 | | 179591 | 1 | | 452 | spam | +-------------------------+------------------+ 3 rows in set (0.41 sec)
The above mentioned SQL query, deletes all the comments from the wp_comments table which have a value of “spam” in comments_approved column.delete from wp_comments where comment_approved="spam"; 452 rows in set (0.0843 sec)
Now, in order to delete the comments using phpMyAdmin, follow the steps below
1.) Login to your phpMyAdmin application.
2.) Select the database specific to your Wordpress Blog.
3.) Click on the tab which says “SQL”.
If you are someone who is fed up of the amount of Spam comments that you get on your blog, i would recommend that you download and install WP-Ban plugin on yourWordpress blog. WP-Ban allows you to ban users by IP, IP Range, host name and referer url from visiting your WordPress’s blog. It will display a custom ban message when the banned IP, IP range, host name or referer url trys to visit you blog. You can also exclude certain IPs from being banned. There will be statistics recordered on how many times they attemp to visit yourblog. It allows wildcard matching too.